Secure Consul¶
For security reasons, we strongly recommend configuring the TLS encryption.
Caution - firewall
We strongly recommend protecting Consul via firewall. Otherwise everyone who may access the Consul Web interface via port 8500 can change the configuration including the user authorization. Only the SEAL Operator servers and maybe the workstations of the system administrators should have access to Consul.
Configure the TLS Encryption¶
The connection to Consul is secured by the TLS certificate located in the /opt/seal/etc/tls directory. That means that after you have replaced the self-signed certificate enclosed in delivery by your own certificate in Secure the SEAL Operator Services the connection to Consul has already been secured.
Specify a CA Certificate (Unnecessary in Most Cases)¶
If a CA certificate has been specified, Consul requires a client certificate from each client, that means from all SEAL Operator services. This would require corresponding properties of the certificate and would be a high effort. A complete explanation of how to use client certificates is beyond the scope of this documentation.
For the rare other cases, this is how you configure a CA certificate with Consul:
-
Open the Consul configuration file:
/opt/seal/etc/consul.json -
Insert the following lines in the first level, for example after the first opening bracket:
{ "ca_file": "/opt/seal/etc/tls/ca.pem", "verify_outgoing": true, ... }Caution - JSON structure
Pay attention to keep the JSON structure in the Consul configuration file! For further information, refer to http://json.org/json-de.html.
-
Save the configuration file.
-
Restart the following service:
seal-consul-agent
Configure ACL¶
Consul comes without ACL (Access Control List) configuration. This is how you configure ACL:
-
Stop SEAL Operator (on every server in case of a cluster).
-
Open the Consul configuration file on the SEAL Operator server (on every server in case of a cluster):
/opt/seal/etc/consul.json -
Insert the following lines in the first level, for example, after the first opening bracket (on every server in case of a cluster):
{ "acl": { "enabled": true, "default_policy": "deny", "enable_token_persistence": true }, ... } -
Start the following service (on every server in case of a cluster):
seal-consul-agent
-
Change to the directory of the Consul program (only on one server in case of a cluster):
cd /opt/seal/seal-consul-agent -
Set the following environment variables (only on one server in case of a cluster):
export CONSUL_HTTP_SSL=true export CONSUL_HTTP_SSL_VERIFY=false -
Execute ACL bootstrap (only on one server in case of a cluster):
./consul acl bootstrapThis results in an output like this:
AccessorID: 770956ae-f0bf-db1d-0dc0-c802b9fdea3a SecretID: 145d39a6-1366-7e3b-496e-fd2f2ea6ae23 Description: Bootstrap Token (Global Management) Local: false Create Time: 2022-01-18 14:33:38.1674571 +0100 CET Policies: 00000000-0000-0000-0000-000000000001 - global-management -
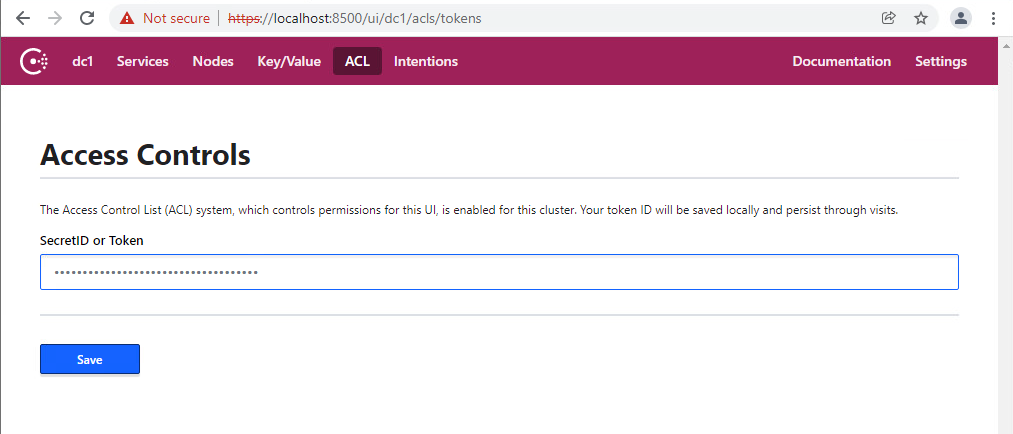
Open the Consul user interface, change to the
ACLtab and enter theSecretIDfrom the bootstrap result (in the example above,145d39a6-1366-7e3b-496e-fd2f2ea6ae23) (only on one server in case of a cluster): -
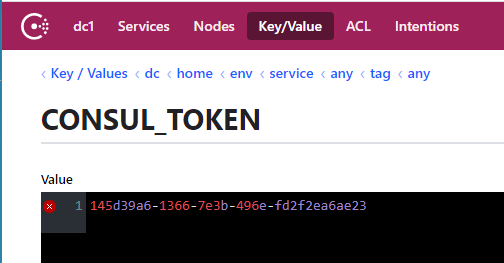
Change to the
Key/Valuetab and specify theSecretIDfrom the bootstrap result (in the example above,145d39a6-1366-7e3b-496e-fd2f2ea6ae23) at thedc/home/env/service/any/tag/any/CONSUL_TOKENkey (only on one server in case of a cluster): -
Open the envconsul configuration file on the SEAL Operator server (on every server in case of a cluster):
/opt/seal/etc/envconsul.json -
Change the value of
consul.tokento theSecretIDfrom the bootstrap result (in the example above,145d39a6-1366-7e3b-496e-fd2f2ea6ae23) (on every server in case of a cluster):{ "consul": { "address": "127.0.0.1:8500", "ssl": { "enabled": true, "verify": false }, "token": "145d39a6-1366-7e3b-496e-fd2f2ea6ae23", "retry": { "attempts": 0 } }, "sanitize": true, "upcase": true, "vault": { "renew_token": false } } -
Stop the following service (on every server in case of a cluster):
seal-consul-agent
-
To enable the services to make DNS requests create the
dns-request-policy.hclfile in an arbitrary directory with the following content (only on one server in case of a cluster):node_prefix "" { policy = "read" } service_prefix "" { policy = "read" } query_prefix "" { policy = "read" } -
Execute the following command to create the policy for DNS requests (only on one server in case of a cluster):
./consul acl policy create -name "dns-requests" -rules @<arbitrary directory>/dns-request-policy.hcl -token 145d39a6-1366-7e3b-496e-fd2f2ea6ae23This results in an output like this:
ID: 4e9cbd04-f18c-237b-6357-e5f6f405b74b Name: dns-requests Description: Datacenters: Rules: node_prefix "" { policy = "read" } service_prefix "" { policy = "read" } query_prefix "" { policy = "read" } -
Execute the following command to create the token for DNS requests (only on one server in case of a cluster):
./consul acl token create -description "Token for DNS Requests" -policy-name dns-requests -token 145d39a6-1366-7e3b-496e-fd2f2ea6ae23This results in an output like this:
AccessorID: 31dee823-61b7-a8ca-fec1-9103ea601a15 SecretID: 9e3f8b90-1c48-1899-8fed-55c94dab6016 Description: Token for DNS Requests Local: false Create Time: 2022-01-31 14:08:31.5254338 +0100 CET Policies: 4e9cbd04-f18c-237b-6357-e5f6f405b74b - dns-requests -
Execute the following command to apply the created token (in the example above,
9e3f8b90-1c48-1899-8fed-55c94dab6016) (only on one server in case of a cluster):./consul acl set-agent-token -token 145d39a6-1366-7e3b-496e-fd2f2ea6ae23 default "9e3f8b90-1c48-1899-8fed-55c94dab6016"This results in an output like this:
ACL token "default" set successfully
Next Step¶
Continue with: Change the Token for Encrypting the Credentials