Keys¶
The key value store of Consul administrates the SEAL Operator configuration.
You can change the key via the Consul Web interface, refer to Consul, or via SEAL Operator CLI, refer to Administrate the System Configuration.
Hint - error messages
Consul has been updated to the version 1.7.4. With this update, the user interface has changed a lot. For example, in the value input dialog, the data is checked for a structure by default and, therefore, you will get error messages in most cases when entering data. In order to avoid these, deactivate the Code switch at the top right.
Units¶
Values with time specifications are specified in the following time units:
-
seconds(s,sec) -
minutes(m,min) -
hours(h,hr) -
days(d) -
weeks(w,wk) -
months -
years(y,yr)
Example - with time units
2 hours and 30 minutes: 2h30m
4 minutes and 2 seconds: 4m2s
ACTION_EXECUTOR¶
ACTION_EXECUTOR specifies the backend system.
The key is available for the following services:
seal-operator-dpfseal-operator-p4seal-operator-p5seal-operator-sharepointseal-preprocess
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/ACTION_EXECUTORdc/home/env/service/operator-p4/tag/any/ACTION_EXECUTORdc/home/env/service/operator-p5/tag/any/ACTION_EXECUTORdc/home/env/service/operator-sharepoint/tag/any/ACTION_EXECUTORdc/home/env/service/preprocess/tag/any/ACTION_EXECUTOR
Available values: String
-
CONVERTConversion
-
DPFDigital Paper Factory
-
MOCKOnly simulation
-
P4PLOSSYS 4 system
-
P5PLOSSYS Output Engine system
-
SHAREPOINTSharePoint system
Default: MOCK
ALLOW_SHARED_ENTRIES¶
ALLOW_SHARED_ENTRIES specifies if public Web Portal shares are enabled.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/ALLOW_SHARED_ENTRIES
Available values: boolean
Default: false
ALLOWED_OIDC_CLIENTS¶
ALLOWED_OIDC_CLIENTS specifies the mapping of permissions to roles specified in the OIDC identity provider.
For examples and the description of available keys and values within the JSON object, refer to Configure Roles.
The key is available for the following services:
seal-operator-fileuploadseal-operator-serverseal-operator-sharepoint
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/ALLOWED_OIDC_CLIENTS
Available values: JSON string format
Default: none
Hint - maintainability
Although the key is available for several services and can be added for each of them, it is advised to consolidate all permissions in one entry at dc/home/env/service/any/tag/any/ALLOWED_OIDC_CLIENTS.
Hint - template
SEAL Operator CLI has functionality to generate a template for this key. For further information refer to Administrate Configuration.
Example - configuration to enable the creation of documents, tasks, panels and Web Portal shares by a technical user on behalf of a real user (for example via a PLOSSYS 4 Webportal printer)
{
"seal-print-client": {
"roles": {
"seal-print-client-user": {},
"techuser": {
"areas": {
"documents": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
},
"tasks": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
},
"panels": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
}
}
}
}
},
"seal-opcli": {
"roles": {
"seal-print-client-user": {},
"techuser": {
"areas": {
"documents": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
},
"tasks": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
},
"panels": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
},
"shares": {
"set-impersonate": {
"views": ["ALL"],
"permissions": ["impersonate"]
}
}
}
}
}
},
"seal-webportal": {
"roles": {
"service-account": {}
}
}
}
API_BASE_URL¶
API_BASE_URL specifies the URL of the server API.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/API_BASE_URL
Available values: String
<api_base_url>
Default: https://api:3008
API_VERSION¶
API_VERSION specifies the version of the server API.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/API_VERSION
Available values: String
<api_version>
Default: v1
APW_URL¶
APW_URL specifies the URL of the APW REST server.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/APW_URL
Available values: String
<apw_url>
Default: https://localhost:8443
AUTH_ADDITIONAL_SCOPES¶
AUTH_ADDITIONAL_SCOPES specifies additional scopes for OAuth 2 (required for Azure AD for example). Multiple scopes are separated by a blank.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_ADDITIONAL_SCOPES
Available values: String
<scope_1> <scope_2> ... <scope_n>
Default: none
AUTH_CLIENT_ID¶
AUTH_CLIENT_ID specifies the client name configured in the OIDC identity provider for retrieving the access token.
Hint - different usage of AUTH_CLIENT_ID and WEBPORTAL_CLIENT_ID
AUTH_CLIENT_ID is used for setting up the seal-operator-server connection, while WEBPORTAL_CLIENT_ID is used only for storing files in the fileupload store.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/AUTH_CLIENT_IDfor all servicesdc/home/env/service/<service>/tag/any/AUTH_CLIENT_IDfor the specific<service>service
Available values: String
<client_id>
Default:
seal-print-clientfor the user interfaceoperatorfor all other services
AUTH_CLIENT_SECRET¶
AUTH_CLIENT_SECRET specifies the client secret for retrieving the OIDC identity provider's access token.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/AUTH_CLIENT_SECRETfor all servicesdc/home/env/service/<service>/tag/any/AUTH_CLIENT_SECRETfor the specific<service>service
Available values: String
<client_secret>
Default: not revealed
AUTH_CLOCK_TOLERANCE¶
AUTH_CLOCK_TOLERANCE specifies the number of seconds allowed as time difference between the OAuth provider and client.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_CLOCK_TOLERANCE
Available values: String
<number_seconds>
Default: 5
AUTH_DEFAULT_SESSION_DURATION¶
AUTH_DEFAULT_SESSION_DURATION specifies the duration of the default session in seconds if the OAuth provider does not expose the refresh_expires_in parameter in the token.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_DEFAULT_SESSION_DURATION
Available values: String
<number_seconds>
Default: 180
AUTH_IDP_CONNECT_TIMEOUT¶
AUTH_IDP_CONNECT_TIMEOUT specifies the timeout for the connection to the OIDC identity provider. The time has to be specified in seconds.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_IDP_CONNECT_TIMEOUT
Avaialble values: String
<number_seconds>
Default: 60
AUTH_IDP_REQUEST_TIMEOUT¶
AUTH_IDP_REQUEST_TIMEOUT specifies the timeout for authentication requests to the OIDC identity provider. The time has to be specified in seconds.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_IDP_REQUEST_TIMEOUT
Avaialble values: String
<number_seconds>
Default: 10
AUTH_ISSUER_URL¶
AUTH_ISSUER_URL specifies the OIDC issuer URL. This URL points to Keycloak for example. For more information about Keycloak used with SEAL Systems products, refer to the SEAL Interfaces for OIDC documentation.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/AUTH_ISSUER_URL
Available values: String
<oidc_issuer_url>
Default: https://localhost:32769/realms/SEAL
Hint - changed AUTH_ISSUER_URL as of Keycloak 21.0.1
As of SEAL-specific Keycloak version 21.0.1, the URL needed for `AUTH_ISSUER_URL has changed.
-
old value:
AUTH_ISSUER_URL=https://<hostname>:32769/auth/realms/SEAL -
new value:
AUTH_ISSUER_URL=https:/<hostname>:32769/realms/SEAL
Hint - changed AUTH_ISSUER_URL as of Keycloak 21.0.1
As of SEAL-specific Keycloak version 21.0.1, the URL needed for AUTH_ISSUER_URL has changed.
-
old value:
AUTH_ISSUER_URL=https://<hostname>:32769/auth/realms/SEAL -
new value:
AUTH_ISSUER_URL=https:/<hostname>:32769/realms/SEAL
AUTH_PROVIDER¶
AUTH_PROVIDER specifies the type of authentification provider for Webportal's users database. This affects user login, Web Portal shares and email notifications.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
- `dc/home/env/service/operator-webportal/tag/any/AUTH_PROVIDER
Available values: String
-
keycloakWhen using Keycloak as OIDC provider and setting
AUTH_PROVIDERaskeycloakonly users registered with that authentification provider can log in or get shares assigned. In this caseKC_ADMIN_BASE_URLandKC_ADMIN_TARGET_REALMneed to be specified as well. -
genericFor any other OIDC provider or if users outside of the Keycloak user data base should get access emails for shares.
Default: generic
AUTH_REDIRECT_PROTOCOL¶
AUTH_REDIRECT_PROTOCOL specifies the transfer protocol.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_REDIRECT_PROTOCOL
Available values: String
-
http -
https
Default: The protocol of the user interface server is used.
AUTH_REFRESH_TOLERANCE¶
AUTH_REFRESH_TOLERANCE specifies the number of seconds after which a token will be refreshed when it is about to expire.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_REFRESH_TOLERANCE
Available values: String
<number_seconds>
Default: 5
AUTH_TOKEN_ENDPOINT¶
AUTH_TOKEN_ENDPOINT specifies the URL of the token endpoint.
The key is available for all connector services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/AUTH_TOKEN_ENDPOINT
Available values: String
<auth_token_endpoint>
Default: The default is retrieved automatically from the OIDC service.
AUTH_TOKEN_TYPE¶
AUTH_TOKEN_TYPE specifies the type of the token used for the authentication against the REST API.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AUTH_TOKEN_TYPE
Available values: String
-
access_tokenThe access token is used.
-
id_tokenThe ID token is used.
Default: access_token
AVAILABLE_LANGUAGES¶
AVAILABLE_LANGUAGES specifies the languages provided to the user in the user interface. With the same name, a language file (<language>.json) has to exist in C:\Program Files\SEAL Systems\seal-operator-ui\dist\assets\i18n on Windows or /opt/seal/seal-operator-ui/dist/assets/i18n on Linux. Multiple languages are separated by comma.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/AVAILABLE_LANGUAGES
Available values: String
<language1>,<language2> ... <languagex>
Default: de,en,fr
BROKER_FORCE_TLS¶
BROKER_FORCE_TLS specifies if the SEAL NATS message broker uses TLS.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_FORCE_TLS
Available values: Boolean
false-
N -
true Y
Default: false
BROKER_SERVERS¶
BROKER_SERVERS specifies the message broker server hosts and ports. Multiple server and port items are separated by commas.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_SERVERS
Available values: String
nats1:4222,nats2:4222,nats3:4222
Default: localhost:4222
BROKER_REJECT_UNAUTHORIZED¶
BROKER_REJECT_UNAUTHORIZED specifies if self-signed TLS certificates from the message broker will be rejected. Only used if BROKER_FORCE_TLS is enabled.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_REJECT_UNAUTHORIZED
Available values: Boolean
true-
Y -
false N
Default: true
BROKER_TOKEN¶
BROKER_TOKEN specifies the message broker access token.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/BROKER_TOKEN
Available values: String
Default: none
Securing SEAL NATS
For more information on how to secure SEAL NATS by token authentication, refer to to the separate SEAL NATS documentation for Windows or Linux.
CHECK_DOC_NAMES¶
CHECK_DOC_NAMES specifies if entries with the same name are allowed in My Documents.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/CHECK_DOC_NAMES
Available values: Boolean
-
YThe entries have to have different names.
(<n>)is appended to duplicate entries. -
NDuplicate entries are allowed.
Default: Y
CLOSE_PANEL_AFTER_START_TASK¶
CLOSE_PANEL_AFTER_START_TASK specifes if the task panel will be closed after starting the task (printing or converting for example).
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/CLOSE_PANEL_AFTER_START_TASK
Available values: Boolean
-
trueThe task panel will be closed.
-
falseThe task panel will stay open.
Default: false
CONNECTOR_FILE_NAME¶
CONNECTOR_FILE_NAME specifies the path and the name of the YAML file containing the configuration of the connectors if SEAL Operator is running in a cloud environment.
Example - connector file
operator:
connectors:
p4:
cstatus: 'on'
serviceName: operator-p4
url: 'https://operator-p4:3000'
scratch:
cstatus: 'on'
serviceName: operator-fileupload
url: 'https://operator-fileupload:3000'
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/CONNECTOR_FILE_NAME
Available values: String
<config_file>
Default: /config/connector.yml
CONNECTOR_PANEL_TIMEOUT¶
CONNECTOR_PANEL_TIMEOUT specifies the timeout the operator-server service waits at most when requesting the panel configuration from a connector.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/CONNECTOR_PANEL_TIMEOUT
Available values: String
<time_interval_and_unit>
Default: 3s
CONSUL_TOKEN¶
CONSUL_TOKEN specifies the ACL token with which the SEAL Operator services authenticate themselves to Consul.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_TOKEN
Available values: String
<token>
Default: none
CONSUL_URL¶
CONSUL_URL specifies the address of the Consul server to which the SEAL Operator services log on.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/CONSUL_URL
Available values: String
consul_url
Default: https://localhost:8500
CREATE_PREVIEW¶
CREATE_PREVIEW specifies if previews are created for the documents in My Documents.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/CREATE_PREVIEW
Available values: Boolean
-
YPreviews are created.
-
NNo previews are created.
Default: Y
Hint - PREVIEW_PAGE_COUNT
By setting the PREVIEW_PAGE_COUNT key, you can define for how many pages of a document the preview will be generated.
CS_TYPE¶
CS_TYPE specifies the used credential store type.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/CS_TYPE
Available values: String
-
noneNo credential store
-
mockOnly simulation
-
mongoStore credentials in MongoDB
Default: mongo
DEFAULT_DPF_SCHEMA¶
DEFAULT_DPF_SCHEMA specifies the path to the JSON schema file containing the configuration of the DPF connector.
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/DEFAULT_DPF_SCHEMA
Available values: String
<path_name>
Default: <dpf_connector_install_dir>/lib/defaultConfig/schema.json
DEFAULT_FILEUPLOAD_PANEL¶
DEFAULT_FILEUPLOAD_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/DEFAULT_FILEUPLOAD_PANEL
Available values: String
<path_name>
Default: <fileupload_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_FILEUPLOAD_SCHEMA¶
DEFAULT_FILEUPLOAD_SCHEMA specifies the path to the JSON schema file containing the configuration of the My Documents connector.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/DEFAULT_FILEUPLOAD_SCHEMA
Available values: String
<path_name>
Default: <fileupload_connector_install_dir>/lib/defaultConfig/settings.json
DEFAULT_P4_PANEL¶
DEFAULT_P4_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/DEFAULT_P4_PANEL
Available values: String
<path_name>
Default: <p4_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_P4_SCHEMA¶
DEFAULT_P4_SCHEMA specifies the path to the JSON schema file containing the configuration of the PLOSSYS 4 connector.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/DEFAULT_P4_SCHEMA
Available values: String
<path_name>
Default: <p4_connector_install_dir>/lib/defaultConfig/settings.json
DEFAULT_P5_PANEL¶
DEFAULT_P5_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-p5 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p5/tag/any/DEFAULT_P5_PANEL
Available values: String
<path_name>
Default: <p5_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_P5_SCHEMA¶
DEFAULT_P5_SCHEMA specifies the path to the JSON schema file containing the configuration of the PLOSSYS Output Engine connector.
The key is available for the seal-operator-p5 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p5/tag/any/DEFAULT_P5_SCHEMA
Available values: String
<path_name>
Default: <p5_connector_install_dir>/lib/defaultConfig/settings.json
DEFAULT_PANEL¶
DEFAULT_PANEL specifies the type of the panel that is opened when opening the user interface and no panel exist yets.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DEFAULT_PANEL
Available values: String
<panel_type>e. g.operator-p4,operator-p5,operator-dpf
Default: none
DEFAULT_SAP_PANEL¶
DEFAULT_SAP_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-sap service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sap/tag/any/DEFAULT_SAP_PANEL
Available values: String
<path_name>
Default: <sap_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_SAP_SCHEMA¶
DEFAULT_SAP_SCHEMA specifies the path to the JSON schema file containing the the configuration of the SAP connector.
The key is available for the seal-operator-sap service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sap/tag/any/DEFAULT_SAP_SCHEMA
Available values: String
<path_name>
Default: <sap_connector_install_dir>/lib/defaultConfig/settings.json
DEFAULT_SHAREPOINT_PANEL¶
DEFAULT_SHAREPOINT_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-sharepoint service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sharepoint/tag/any/DEFAULT_SHAREPOINT_PANEL
Available values: String
<path_name>
Default: <sharepoint_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_SHAREPOINT_SCHEMA¶
DEFAULT_SHAREPOINT_SCHEMA specifies the path to the JSON schema file containing the configuration of the SharePoint connector.
The key is available for the seal-operator-sharepoint service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sharepoint/tag/any/DEFAULT_SHAREPOINT_SCHEMA
Available values: String
<path_name>
Default: <sharepoint_connector_install_dir>/lib/defaultConfig/settings.json
DEFAULT_WEBPORTAL_PANEL¶
DEFAULT_WEBPORTAL_PANEL specifies the path to the JSON schema file containing the configuration of the panel.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/DEFAULT_WEBPORTAL_PANEL
Available values: String
<path_name>
Default: <webportal_connector_install_dir>/lib/defaultConfig/panel.json
DEFAULT_WEBPORTAL_SCHEMA¶
DEFAULT_WEBPORTAL_SCHEMA specifies the path to the JSON schema file containing the configuration for the Web Portal connector.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/DEFAULT_WEBPORTAL_SCHEMA
Available values: String
<path_name>
Default: <webportal_connector_install_dir>/lib/defaultConfig/settings.json
Hint - public-settings.json
If the public access option is enabled, use the provided public-settings.json instead.
DISABLE_ADD_FAVORITE¶
DISABLE_ADD_FAVORITE specifies if the button for adding a favorite panel is available.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_ADD_FAVOURITE
Available values: Boolean
-
trueThe favorite panel button is hidden.
-
falseThe favorite panel button is shown.
Default: false
DISABLE_ADD_PANEL¶
DISABLE_ADD_PANEL specifies if the Add Panel button is available in the menu on the left.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_ADD_PANEL
Available values: Boolean
-
trueThe
Add Panelbutton is hidden. -
falseThe
Add Panelbutton is shown.
Default: false
DISABLE_LATEST_TASKS¶
DISABLE_LATEST_TASKS specifies if the list containing the latest tasks is available in the menu on the left.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_LATEST_TASKS
Available values: Boolean
true
The last tasks list is hidden.
false
The last tasks list is shown.
Default: false
DISABLE_MESSAGES¶
DISABLE_MESSAGES specifies if the message panel is available.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_MESSAGES
Available values: Boolean
-
trueThe message panel is hidden.
-
falseThe message panel is shown.
Default: false
DISABLE_MY_LISTS_ACCESS¶
DISABLE_MY_LISTS_ACCESS specifies if the My Lists list is available in the menu on the left.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_MY_LISTS_ACCESS
Available values: Boolean
-
trueThe
My Listslist is hidden. -
falseThe
My Listslist is shown.
Default: false
DISABLE_REMOVE_PANEL¶
DISABLE_REMOVE_PANEL specifies if the button for removing a panel is available.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_REMOVE_PANEL
Available values: Boolean
-
trueThe removing panel button is hidden.
-
falseThe removing panel button is shown.
Default: false
DISABLE_TASK_NOTIFICATIONS¶
DISABLE_TASK_NOTIFICATIONS specifies if the task notification item is available in the menu on the left.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DISABLE_TASK_NOTIFICATIONS
Available values: Boolean
-
trueThe task notification item is hidden.
-
falseThe task notification item is shown.
Default: false
DETAILS_DISABLE_METADATA¶
DETAILS_DISABLE_METADATA specifies if the metadata editor is available in the details panel of the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DETAILS_DISABLE_METADATA
Available values: Boolean
-
trueThe metadata editor in the details panel is hidden.
-
falseThe metadata editor in the details panel is shown.
Default: false
DETAILS_DISABLE_TOOLBAR¶
DETAILS_DISABLE_TOOLBAR specifies if the toolbar is available in the details panel of the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/DETAILS_DISABLE_TOOLBAR
Available values: Boolean
-
trueThe toolbar in the details panel is hidden.
-
falseThe toolbar in the details panel is shown.
Default: false
DOCUMENT_STREAM¶
DOCUMENT_STREAM specifies if the documents in a task should be printed as a document stream in PLOSSYS Output Engine without being interrupted by other documents.
The key is available for the seal-operator-p5 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p5/tag/any/DOCUMENT_STREAM
Available values: Boolean
-
YDocuments are printed as a document stream. In PLOSSYS Administrator, those jobs are marked with a
Bnext to the job icon. -
NDocuments are not printed as a document stream.
Default: Y
DOCUMENT_TRANSFER_RETRIES¶
DOCUMENT_TRANSFER_RETRIES specifies the number of retries for transferring a document to the backend system if the transfer fails.
The key is available for the following services:
seal-operator-p4seal-operator-p5seal-operator-dpf
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/DOCUMENT_TRANSFER_RETRIESdc/home/env/service/operator-p5/tag/any/DOCUMENT_TRANSFER_RETRIESdc/home/env/service/operator-dpf/tag/any/DOCUMENT_TRANSFER_RETRIES
Available values: Integer
<retries>
Default: 5
DPF_URL¶
DPF_URL specifies the URL for the REST calls for DPF.
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/DPF_URL
Available values: String
dpf_rest_url
Default: https://localhost:9126/rest/dpf
EMAIL_SERVICE_URL¶
EMAIL_SERVICE_URL specifies the URL of the email service used for WebPortal notification emails.
The key is available for the seal-operator-webportal.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/EMAIL_SERVICE_URL
Available values: String
<emailservice_url>
Default: none
EMAIL_FROM¶
EMAIL_FROM is used in the Web Portal context. It specifies the sender email address which is used for the notification emails regarding shares provided or accessed.
The key is available for the seal-email-service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
- `dc/home/env/service/email-service/tag/any/EMAIL_FROM
Available values: String
<sender_email_address>
Default: none
FEAT_ACTION_MOCK_INPUT¶
FEAT_ACTION_MOCK_INPUT specifies if the DPF simulator reads the document content from fileupload.
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/FEAT_ACTION_MOCK_INPUT
Available values: Boolean
Default: Y
FEAT_ACTION_MOCK_OUTPUT¶
FEAT_ACTION_MOCK_OUTPUT specifies if the DPF simulator writes the result document content to fileupload.
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/FEAT_ACTION_MOCK_OUTPUT
Available values: Boolean
Default: Y
FEAT_LOG_NATSINFO¶
FEAT_LOG_NATSINFO enables additional log messages concerning the initialization of the NATS message broker.
The key is available for all services.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/any/tag/any/FEAT_LOG_NATSINFO
Available values: Boolean
-
true
Enables additional log messages
-
false
Disables additional log messages
Default: false
FEAT_TASK_STATUS¶
FEAT_TASK_STATUS specifies if the task status may be set via a REST call by third party applications.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/FEAT_TASK_STATUS
Available values: Boolean
-
YThird party applications may set the task status via a REST call.
-
NOnly the
operator-serverservice is allowed to set the task status.
Default: N
FILESTORE_TYPE¶
FILESTORE_TYPE specifies the location where the content of the uploaded files is stored.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/FILESTORE_TYPE
Available values: String
gridfs
The file content is stored in MongoDB.
s3
The file content is stored in S3 used in AWS, for example. For the further configuration, refer to Connect S3.
Default: gridfs
HIDE_LEFT_MENU¶
HIDE_LEFT_MENU specifies if the left menu will be open or closed at the beginning.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/HIDE_LEFT_MENU
Available values: Boolean
-
trueThe left menu is closed at the beginning.
-
falseThe left menu is open at the beginning.
Default: false
HOUSEKEEPER_INTERVAL¶
HOUSEKEEPER_INTERVAL is available for the seal-operator-fileupload and seal-operator-webportal services. For seal-operator-fileupload service it specifies the time after which documents in the My Documents panel are obsolete. For the seal-operator-webportal service it specifies the time after which expired webportal shares are obsolete. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
seal-operator-fileuploadseal-operator-webportal
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/HOUSEKEEPER_INTERVALdc/home/env/service/operator-webportal/tag/any/HOUSEKEEPER_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 1h
HOUSEKEEPER_SWEEP_AGE¶
HOUSEKEEPER_SWEEP_AGE for seal-operator-fileupload service specifies the minimum age of documents to be deleted from the My Documents panel. If the key is set for seal-operator-webportal service it specifies the minimum time after which of expired webportal shares are deleted. The value has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the following services:
seal-operator-fileuploadseal-operator-webportal
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/HOUSEKEEPER_SWEEP_AGEdc/home/env/service/operator-webportal/tag/any/HOUSEKEEPER_SWEEP_AGE
Available values: String
<time_interval_and_unit>
Default:
3dforoperator-fileupload7dforoperator-webportal
HTPASSWD¶
HTPASSWD specifies the credentials of the SharePoint technical user in htpasswd format.
The key is available for the seal-operator-sharepoint service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sharepoint/tag/any/HTPASSWD
Available values: String
<name>:<password>
Default: none
ID_PROVIDER_CERT¶
ID_PROVIDER_CERT specifies the path and the file name of the certificate generated by the OIDC identity provider.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/ID_PROVIDER_CERT
Available values: String
<path_name>
Default: none
ID_PROVIDER_NAME¶
ID_PROVIDER_NAME specifies the name of the OIDC identity provider. When using more than one OIDC identity providers, separate them by a blank.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/ID_PROVIDER_NAME
The key is mandatory.
Available values: String
-
<id_provider_name>(For example, with Keycloak, it is a complete URL:https://<hostname>:32769/realms/SEAL) -
<id_provider_name_1> <id_provider_name_2>(For example, with Keycloak, they are complete URLs:https://<cluster internal hostname>:32769/realms/SEAL https://<cluster external hostname>:32769/realms/SEAL)
Default: none
Hint - changed ID_PROVIDER_NAME as of Keycloak 21.0.1
As of SEAL-specific Keycloak version 21.0.1, the URL needed for ID_PROVIDER_NAME has changed.
-
old value:
ID_PROVIDER_NAME=https://<hostname>:32769/auth/realms/SEAL -
new value:
ID_PROVIDER_NAME=https://<hostname>:32769/realms/SEAL
IMPERSONATE_TOKEN_OWNER¶
IMPERSONATE_TOKEN_OWNER specifies the JSON Web token key containing the owner. This is used for the impersonate functionality.
The key is available for the following services:
seal-operator-fileuploadseal-operator-serverseal-operator-sharepoint
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/IMPERSONATE_TOKEN_OWNERdc/home/env/service/operator-server/tag/any/IMPERSONATE_TOKEN_OWNERdc/home/env/service/operator-sharepoint/tag/any/IMPERSONATE_TOKEN_OWNER
Available values: String
<token-key>
Default: preferred_username
INFOSERVER_URL¶
INFOSERVER_URL specifies the URL of PLOSSYS Infoserver.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<infoserver_url>
Default: socket://localhost:7125
ITEM_TYPE¶
ITEM_TYPE specifies the type of items to be collected by the TreeResolver connector.
The key is available for the seal-operator-treeresolver service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-treeresolver/tag/any/ITEM_TYPE
Available values: String
-
documentOnly documents are taken into account.
-
folderOnly directories are taken into account.
-
allBoth documents and directories are taken into account.
Default: document
JWT_LOG_TOKEN¶
Logs the token-set in debug level if set. If log level is info or something lower than debug nothing is logged.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/JWT_LOG_TOKEN
Available values: Boolean
-
YThe token-set is logged.
-
NThe token-set is not logged.
Default: N
JWT_ROLES¶
JWT_ROLES specifies the property name set in the JSON Web Token (JWT) for accessing the user roles.
The key is available for all services.
In Consul, the key is specified here:
dc/home/env/service/any/tag/any/JWT_ROLES
Available values: String
<property_name>
Default: none
JWT_USERNAME¶
JWT_USERNAME specifies the property name set in the JSON Web Token (JWT) for accessing the user name in the current output job.
The key is available for the following services:
seal-operator-p4seal-operator-p5
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/JWT_USERNAMEdc/home/env/service/operator-p5/tag/any/JWT_USERNAME
Available values: String
<user_name>
Default: sub
KC_ADMIN_BASE_URL¶
KC_ADMIN_BASE_URL specifies the admin base url if Keycloak is used as an OIDC provider and AUTH_PROVIDER is set as keycloak.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/KC_ADMIN_BASE_URL
Available values: String
<keycloak_base_url>
Default: 'https://localhost:32769/auth'
Hint - changed URL as of Keycloak 21.0.1
As of SEAL-specific Keylcloak version 21.0.1, the URL needed for KC_ADMIN_BASE_URL has changed.
- old value:
https://<hostname>:32769/auth - new value:
https://<hostname>:32769
KC_ADMIN_TARGET_REALM¶
KC_ADMIN_TARGET_REALM specifies the target realm if Keycloak is used as an OIDC provider and AUTH_PROVIDER is set as keycloak.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/KC_ADMIN_TARGET_REALM
Available values: String
<keycloak_target_realm>
Default: 'SEAL'
LISTITEM_NAME¶
LISTITEM_NAME specifies the name of the property used as a list item name.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/LISTITEM_NAME
Available values: String
<property>
Default: metadata.name
LOG_DELETED_TASK_ITEMS¶
LOG_DELETED_TASK_ITEMS specifies if on deleting task input items this deletion is logged in the deletedInputItems task parameter.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/LOG_DELETED_TASK_ITEMS
Available values: Boolean
-
YThe deletion of task input items is logged in the
deletedInputItemstask parameter. -
NThe deletion of task input items is not logged.
Default: N
LOG_LEVEL¶
LOG_LEVEL specifies the log level for the correspondent service. Messages that correspond to this log level or a higher one are written to the log file.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/LOG_LEVELfor all servicesdc/home/env/service/<service>/tag/any/LOG_LEVELfor the specific<service>service
Available values: String
-
debugDebug messages are written to the log file of the service.
-
infoInformation messages are written to the log file of the service.
-
warnWarnings are written to the log file of the service.
-
errorError messages are written to the log file of the service.
-
fatalMessages about serious errors are written to the log file of the service.
Default: info
Example - log level error
Messages of the log levels error and fatal are written to the log file.
Example - log level info
Messages of the log levels info, warn, error and fatal are written to the log file.
MESSAGE_TIMEOUT¶
MESSAGE_TIMEOUT specifies the time interval after that the messages will be deleted. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/MESSAGE_TIMEOUT
Available values: String
<time_interval_and_unit>
Default: 1h
MESSAGE_TTL¶
MESSAGE_TTL specifies how long the messages will be stored. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/MESSAGE_TTL
Available values: String
<time_interval_and_unit>
Default: 24h
MESSAGES_MAX_RETRIES¶
MESSAGES_MAX_RETRIES specifies the maximum number of attempts for notification callbacks in the seal-operator-message-relay service. A value of 0 means, there is no maximum and a notification callback is tried endlessly until it succeeds.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MESSAGES_MAX_RETRIES
Available values: Integer
<maximum_retries>
Default: 0
Literature - use case description
For further information refer to the use case description Create Callback Actions.
MESSAGES_OBEY_SEQUENCE¶
MESSAGES_OBEY_SEQUENCE specifies if in case of a failing notification callback the seal-operator-message-relay service retries the failing callback until it succeeds without executing other callbacks within the retry interval or postpones the failing callback executing other callbacks within the retry interval.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MESSAGES_OBEY_SEQUENCE
Available values: Boolean
-
YObey notification sequence
-
NDo not obey notification sequence
Default: N
Literature - use case description
For further information refer to the use case description Create Callback Actions.
MESSAGES_REQUEST_TIMEOUT¶
MESSAGES_REQUEST_TIMEOUT specifies the time after which a callback request fails with timeout. The time has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MESSAGES_REQUEST_TIMEOUT
Available values: String
<timeout_and_unit>
Default: 20s
Literature - use case description
For further information refer to the use case description Create Callback Actions.
MESSAGES_RETRY_INTERVAL¶
MESSAGES_RETRY_INTERVAL specifies the time interval after which the seal-operator-message-relay service retries a failing notification callback. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MESSAGES_RETRY_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 30s
Literature - use case description
For further information refer to the use case description Create Callback Actions.
MONGO_CONNECT_RETRIES¶
MONGO_CONNECT_RETRIES specifies how often the service attempts to connect to the database.
The key is available for all services using MongoDB.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/MONGO_CONNECT_RETRIES
Available values: Integer
<retries>
Default: 10
MONGO_FILEUPLOAD_URL¶
MONGO_FILEUPLOAD_URL specifies the URL of the MongoDB for file uploads into My Documents.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/MONGO_FILEUPLOAD_URL
Available values: String
<fileupload_url>
Default: mongodb://localhost:27017/operator-fileupload
MONGO_LOCKS_AGE¶
MONGO_LOCKS_AGE specifies the time interval after which a lock is regarded as outdated and deleted from the database. A quarter of MONGO_LOCKS_AGE is used as lock-update interval. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MONGO_LOCKS_AGE
Available values: String
<time_interval_and_unit>
Default: 1m
MONGO_LOCKS_INTERVAL¶
MONGO_LOCKS_INTERVAL specifies the time interval after which the ages of the locks are checked. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MONGO_LOCKS_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 5s
MONGO_MESSAGE_RELAY_URL¶
MONGO_MESSAGE_RELAY_URL specifies the URL of the MongoDB for storing and retrieving notifications.
The key is available for the seal-operator-message-relay, seal-operator-server and seal-operator-webportal services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/MONGO_MESSAGE_RELAY_URLdc/home/env/service/operator-server/tag/any/MONGO_MESSAGE_RELAY_URLdc/home/env/service/operator-webportal/tag/any/MONGO_MESSAGE_RELAY_URL
Available values: String
<mongodb_url>
Default: mongodb://localhost:27017/operator-message-relay
MONGO_SERVER_URL¶
MONGO_SERVER_URL specifies the URL of the MongoDB.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/MONGO_SERVER_URL
Available values: String
<mongodb_url>
Default: mongodb://localhost:27017/operator-server
MONGO_TOKEN¶
MONGO_TOKEN specifies the key for credential encryption and decryption.
The key is available for the seal-operator-server service.
MONGO_TOKEN is only used when CS_TYPE is set to mongo.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/MONGO_TOKEN
Available values: String
<token>
Default: not revealed
MONGO_UI_URL¶
MONGO_UI_URL specifies the URL of the MongoDB for storing session information.
The key is available for the seal-operator-ui and seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/MONGO_UI_URLdc/home/env/service/operator-server/tag/any/MONGO_UI_URL
Available values: String
<mongodb_url>
Default: mongodb://localhost:27017/operator-ui
NODE_TLS_REJECT_UNAUTHORIZED¶
NODE_TLS_REJECT_UNAUTHORIZED specifies if self-signed certificates are allowed.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/NODE_TLS_REJECT_UNAUTHORIZED
Available values: Integer
-
0Self-signed certificates are allowed.
-
1Self-signed certificates are not allowed.
Default: 1
Caution - security gap
Setting NODE_TLS_REJECT_UNAUTHORIZED to 0 in a productive system is a serious security gap! Only use it for test purposes!
Hint - certificate
Unless NODE_TLS_REJECT_UNAUTHORIZED is set to 0 or specified at all, the certificate has to contain the correct IP address or hostname since this is used for the authorization check.
NOTIFICATION_CALLBACKS¶
NOTIFICATION_CALLBACKS specifies callback actions for particular events like task or document updates.
The key is available for the seal-operator-notifier service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-notifier/tag/any/NOTIFICATION_CALLBACKS
Available values: JSON string format
Default: none
Available message types:
-
ADD_TASK -
UPDATE_TASK -
REMOVE_TASK -
UPDATE_DOCUMENT
Available action parameters:
-
action: stringMandatory, contains the callback URI. If the specified protocoll is a valid URL protocoll like
httporhttps, the specified callback URI will be taken as a URL and aPOSTrequest will be generated per default. If another HTTP request method likeGET,PUTorPATCHshould be used instead, themethodparameter has to be set as well. The notification message will be sent as request body (as long as the request method is notGET). -
entireItem: booleanfalseDefault. Only essential object data (likescope,source,sub) and changed object data will be sent.trueThe entire object (task, document) will be sent. -
key: stringA specific parameter key that has to be contained in the message, f.e.
status. Only in combination with thevalueparameter. -
value: stringSpecific parameter value, that has to be set as value for the specified
keyparameter. Can be a regular expression, f.e..*p402.*. -
method: stringHTTP request method to be used, default:
POST.
Example - different callback actions depending on the status of the updated task
{
"UPDATE_TASK": [
{
"key": "status",
"value": "processing",
"action": "http://external.web.site.com/running"
},
{
"key": "status",
"value": "completed",
"action": "http://external.web.site.com/success"
},
{
"key": "status",
"value": "failed",
"action": "http://external.web.site.com/error",
"entireItem": true
}
]
}
Literature - use case description
For further information and examples, refer to the use case description Create Callback Actions.
ONLINE_DOCS_URL¶
ONLINE_DOCS_URL specifies the URL pointing to a external documentation.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/ONLINE_DOCS_URL
Available values: String
<docs_url>
Default: ``
Example - URL for a PDF file
https://www.sealsystems.de/fileadmin/mediaFiles/OtherFiles/Downloads/Doku/TOOLS/systemmonitoring_tec_de.pdf
OPERATOR_UI_PORT¶
OPERATOR_UI_PORT specifies the port for accessing the seal-operator-ui service.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/OPERATOR_UI_PORT
Available values: String
<port_number>
Default: 3000
OPERATOR_SERVER_SERVICE¶
OPERATOR_SERVER_SERVICE specifies the name of the operator-server service as it is registered in Consul.
The key is available for all connector services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/OPERATOR_SERVER_SERVICE
Available values: String
<operator_name>
Default: operator-server
OPERATOR_SERVER_URL¶
OPERATOR_SERVER_URL specifies the URL of the Operator server.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/OPERATOR_SERVER_URL
Available values: String
<operator_url>
Default: https://localhost:3008
PANEL_DISABLE_ACTIONS¶
PANEL_DISABLE_ACTIONS specifies the standard actions to be disabled in the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/PANEL_DISABLE_ACTIONS
Available values: Comma-separated strings
'down', 'up', 'paste', 'delete', 'view', 'save'
Default: ``
PANEL_DISABLE_DROP_AREA¶
PANEL_DISABLE_DROP_AREA specifies if the file drag&drop area is available in the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/PANEL_DISABLE_DROP_AREA
Available values: Boolean
-
trueThe file drag&drop area is hidden.
-
falseThe file drag&drop item is shown.
Default: false
PANEL_DISABLE_METADATA¶
PANEL_DISABLE_METADATA specifies if the metadata editor is available in the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/PANEL_DISABLE_METADATA
Available values: Boolean
-
trueThe metadata editor is hidden.
-
falseThe metadata editor is shown.
Default: false
PANEL_DISABLE_START_BUTTON¶
PANEL_DISABLE_START_BUTTON specifies if the start (print or convert) button is available in the active panel.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/PANEL_DISABLE_START_BUTTON
Available values: Boolean
-
trueThe start button is hidden.
-
falseThe start button is shown.
Default: false
PANEL_DISABLE_STATUS¶
PANEL_DISABLE_STATUS specifies if the panel status of the active panel is shown in the panel header.
The key is available for the seal-operator-ui service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-ui/tag/any/PANEL_DISABLE_STATUS
Available values: Boolean
-
trueThe panel status is hidden.
-
falseThe panel status is shown.
Default: false
PGHOST¶
PGHOST specifies the server name of the PLOSSYS 4 PostgreSQL database used for the job reply.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<plossys_netdome_server_name>
Default: localhost
PGPORT¶
PGPORT specifies the port number of the PLOSSYS 4 PostgreSQL database used for the job reply.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<plossys_netdome_port>
Default: 7128
PLOSSYS_IPP_URL¶
PLOSSYS_IPP_URL specifies the URL of the checkin service of the PLOSSYS Output Engine system.
The key is available for the seal-operator-p5 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p5/tag/any/PLOSSYS_IPP_URL
Available values: String
<ipp_checkin_url>
Default: ipp://localhost:631
PLOSSYS_NAME¶
PLOSSYS_NAME specifies an arbitrary unique name of a PLOSSYS 4 backend system in case of multiple backend systems.
Hint - multiple PLOSSYS 4 systems
For further information refer to Multiple PLOSSYS 4 Backends.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/SYSTEM/<system_no>/PLOSSYS_NAME
Available values: String
<plossys_4_server_name>
Default: Hostname from PLOSSYS_URL
PLOSSYS_TIMEOUT¶
PLOSSYS_TIMEOUT specifies the timeout for connecting and retrieving data from a PLOSSYS 4 system. The minimum value is two seconds. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/PLOSSYS_TIMEOUT
Available values: String
<time_interval_and_unit>
Default: 10s
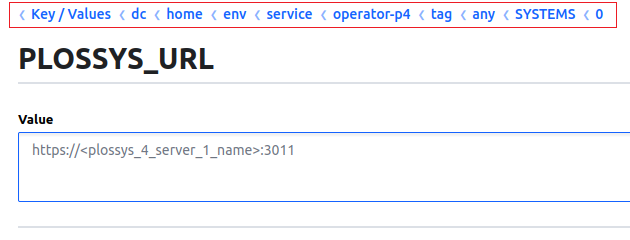
PLOSSYS_URL¶
PLOSSYS_URL specifies the URL of the PLOSSYS 4 system to which SEAL Operator has to connect.
Hint - multiple PLOSSYS 4 systems
In case of multiple PLOSSYS 4 systems the configuration differs, refer to SYSTEMS and Multiple PLOSSYS 4 Backends.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/PLOSSYS_URL
Available values: String
<plossys_netdome_url>
Default: https://localhost:3011
PLSHOST¶
PLSHOST specifies the server name of PLOSSYS Infoserver.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<infoserver_server_name>
Default: localhost
PLSPORT¶
PLSPORT specifies the port number of PLOSSYS Infoserver.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<infoserver_port>
Default: 7125
PLSROOT¶
PLSROOT specifies the PLOSSYS 4 installation directory.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<plossys_netdome_dir>
Default:
-
Windows:
c:\SEAL\applications -
Linux: home directory of the user that runs the service, also defined as $HOME system variable.
POLLING_INTERVAL¶
POLLING_INTERVAL specifies the time interval after which the seal-operator-message-relay service checks for new notifications. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-message-relay service.
In Consul, the key is specified here. If the key does not yet exist, you have to create it:
dc/home/env/service/operator-message-relay/tag/any/POLLING_INTERVAL
Available values: String
<time_interval_and_unit>
Default: 3s
PREVIEW_PAGE_COUNT¶
PREVIEW_PAGE_COUNT specifies the number of preview pages of a document will be created upon adding it to a panel.
The key is available for the seal-operator-fileupload service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/PREVIEW_PAGE_COUNT
Available values: String
<number_of_pages>
Default: 1
Hint - preview_page_count in panel.json
If you want to increase the number of preview pages in an SEAL Operator panel, you need to set the preview_page_count variable in the configuration file set for the DEFAULT_<connector>_PANEL key. Make sure, CREATE_PREVIEW is not set to N.
Already existing previews will not be generated anew when either of the values ist changed.
For an example on how to set the variable in the panel.json file, refer to Number of Preview Pages.
PUBLIC_SERVICES¶
PUBLIC_SERVICES specifies which repository services are open for public access, for example operator-webportal or operator-fileupload. When enabled, access to files or folders is possible via link. This access is restricted to GET requests.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/PUBLIC_SERVICES
Available values: Comma-separated strings
Default: none
PULSE_DOC_EXPORT¶
PULSE_DOC_EXPORT specifies a space separated list of DPF pulse job configurations for which document data has to be exported to DPF. The value has to always include both default export configurations pulse.publish and pulse.coversheet. Any additional job configuration can be added to it.
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/PULSE_DOC_EXPORT
Available values: String
Default: pulse.publish pulse.coversheet
Example - configuration with an additional job configuration
env:
service:
operator-dpf:
tag:
any:
PULSE_DOC_EXPORT: `pulse.publish pulse.coversheet pulse.foo`
...
RLI_JOBNAME_KEY¶
RLI_JOBNAME_KEY contains the name of a key in repro list files whose value is used as job name in SEAL Print Client. Unless the specified key exists in the repro list file, PLS_PLOTID, PLS_ORIG_NAME and a self-generated UUID are used in this order.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/RLI_JOBNAME_KEY
Available values: String
<rli_key>
Default: name
RLI_STOP_ON_ERROR¶
RLI_STOP_ON_ERROR specifies if on any document error the creation of a DPF job is stopped or if the error is logged into the reprolist document data (only for creating DPF job via RLI).
The key is available for the seal-operator-dpf service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-dpf/tag/any/RLI_STOP_ON_ERROR
Available values: Boolean
-
YThe creation of a DPF job is stopped on any document error.
-
NThe creation of a DPF job is continued on any document error and the error is logged into the reprolist.
Default: N
RLIGATE¶
RLIGATE specifies the name of the target directory for the repro list files (rli, rlist) without path. The correspondent path is determined from the PLOSSYS 4 environment.
The key is available for the node-p4rest service.
The key is specified as system variable when installing the REST package in the PLOSSYS 4 system.
Available values: String
<gate_name>
Default: rlipdmgate
S3_ACCESS_KEY_ID¶
S3_ACCESS_KEY_ID specifies the ID of the access key used by the seal-operator-fileupload service for accessing the S3 system.
The key is available for the seal-operator-fileupload service.
S3_ACCESS_KEY_ID is only used when FILESTORE_TYPE is set to s3.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/S3_ACCESS_KEY_ID
Available values: String
<s3_access_key_id>
Default: none
S3_BUCKET¶
S3_BUCKET specifies the name of the S3 bucket used by the seal-operator-fileupload service for storing the files, for example, seal-operator-fileupload.
The key is available for the seal-operator-fileupload service.
S3_BUCKET is only used when FILESTORE_TYPE is set to s3.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/S3_BUCKET
Available values: String
<s3_bucket>
Default: seal-operator-fileupload
S3_REGION¶
S3_REGION specifies the S3 region used by the seal-operator-fileupload service for storing the files, for example, eu-central-1.
The key is available for the seal-operator-fileupload service.
S3_REGION is only used when FILESTORE_TYPE is set to s3.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/S3_REGION
Available values: String
<s3_region>
Default: eu-central-1
S3_SECRET_ACCESS_KEY¶
S3_SECRET_ACCESS_KEY specifies the secret of the access key used by the seal-operator-fileupload service for accessing the S3 system.
The key is available for the seal-operator-fileupload service.
S3_REGION is only used when FILESTORE_TYPE is set to s3.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/S3_SECRET_ACCESS_KEY
Available values: String
<s3_access_key_secret>
Default: none
SAP_URL¶
SAP_URL specifies the URL for the SAP system.
The key is available for the seal-operator-sap service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sap/tag/any/SAP_URL
Available values: String
<sap_url>
Default: none
SERVICE_DISCOVERY¶
SERVICE_DISCOVERY specifies if SEAL Operator is running in a cloud environment or on premise.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/SERVICE_DISCOVERY
Available values: String
-
cloudSEAL Operator is running in a cloud environment.
-
consulSEAL Operator is running on premise.
Default: consul
SERVICE_DISCOVERY_PORT¶
SERVICE_DISCOVERY_PORT specifed the HTTPS port under which all services are available in a cloud environment.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/SERVICE_DISCOVERY_PORT
Available values: Integer
<port>
Default: 3000
SERVICE_NAME¶
SERVICE_NAME specifies the name of the service used with the connector.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/SERVICE_NAME
Available values: String
<service_name>
Default: none
SERVICE_URL¶
SERVICE_URL specifies how a service can be accessed.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/<service>/tag/any/SERVICE_URLfor the specific<service>service
Available values: String
<url>
Default: https://localhost:<service_port>
Hint - port list
Default: The server name is determined when a service is started and the default port is used. The correspondent assignment is described in Used Ports.
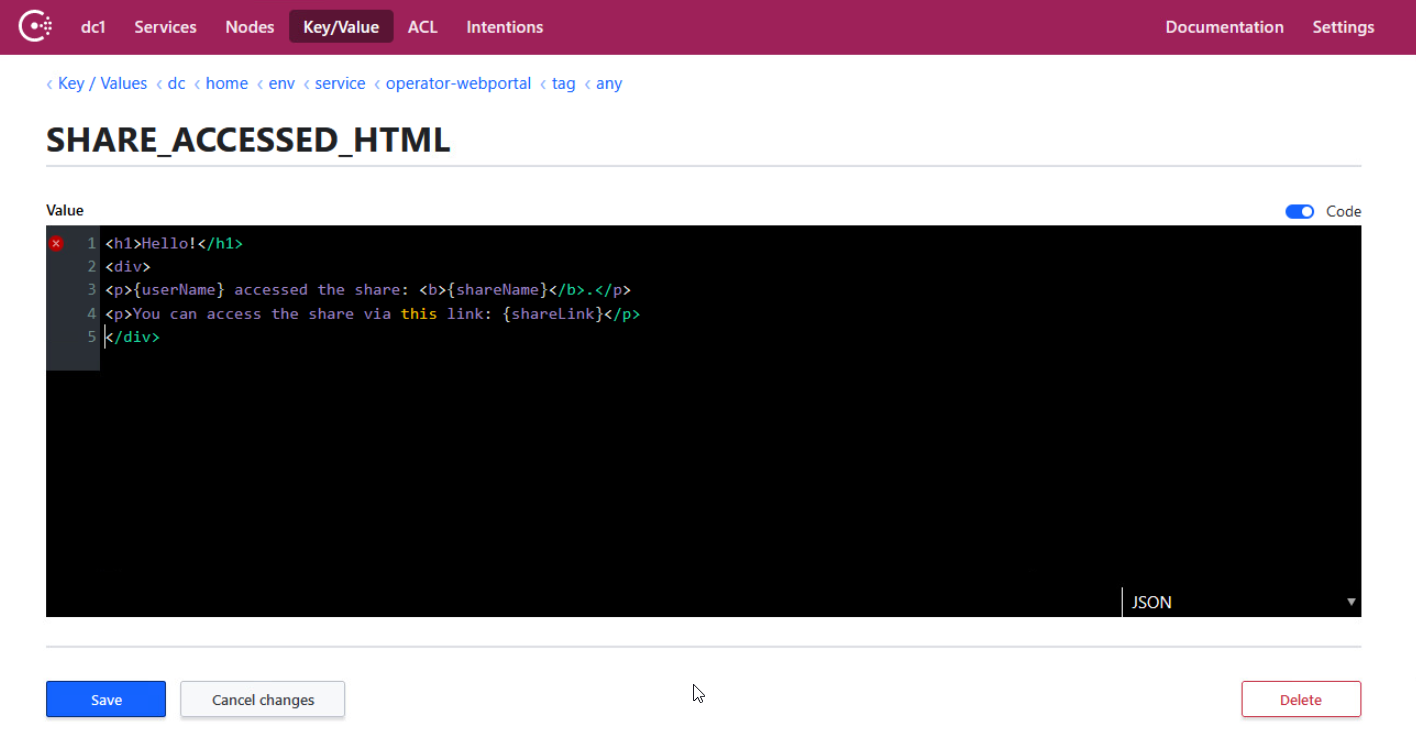
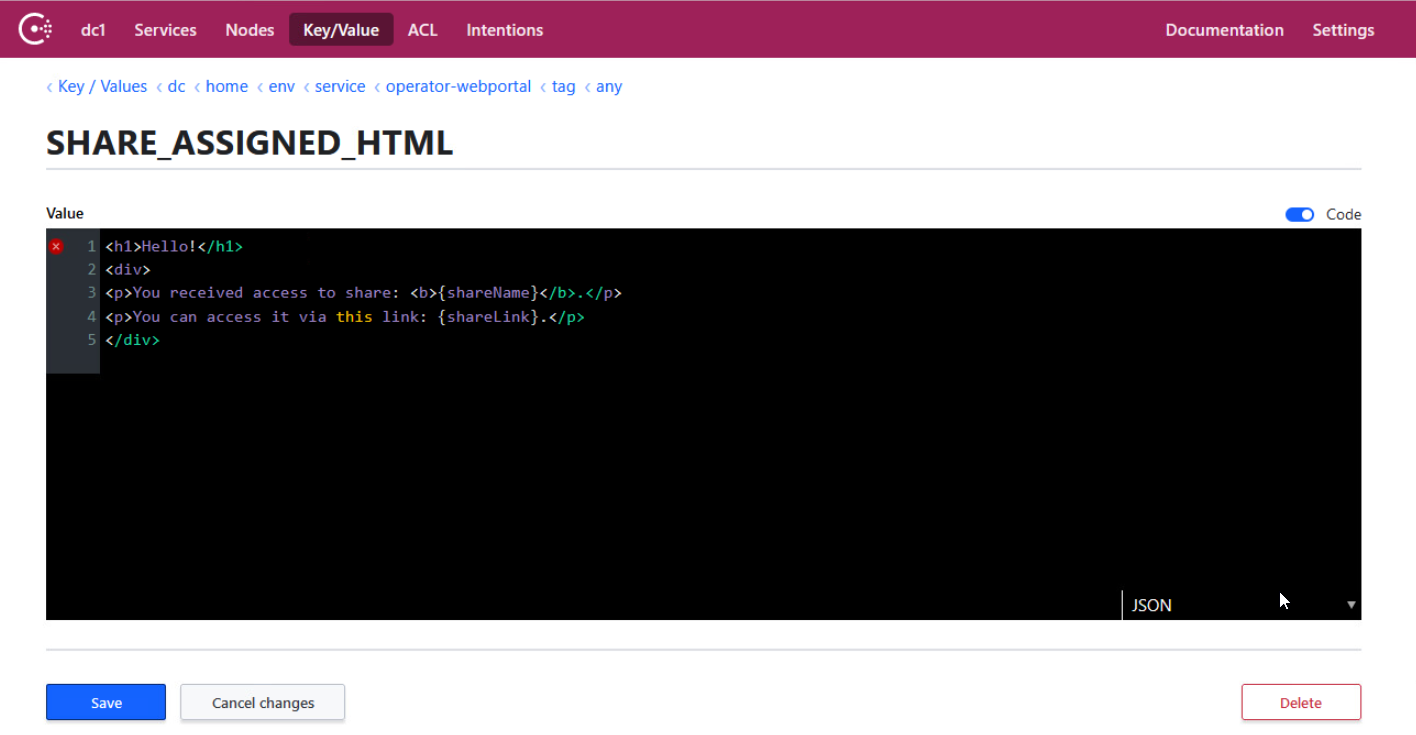
SHARE_ACCESSED_HTML¶
SHARE_ACCESSED_HTML specifies the HTML template for emails sent to the owner of a Web Portal share if the share gets accessed by an assignee for the first time and seal-email-service is enabled.
The key is available for the seal-operator-webportal service.
example
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ACCESSED_HTML
Available Value: string (HTML)
Available placeholders:
-
{shareId}: ID of the share. If both, public and private links to shares should be sent, it is adviced to use the{shareLink}placeholder instead. For the structure of private and public links, refer to the examples for SHARE_ACCESSED_TEXT. -
{shareLink}: Automatically generated link to the share. Depending on whether the share is private or public either a private or a public link will be generated. -
{shareName}: Name of the share given by the creator of the share. -
{userName}: Name of the user who accessed the share. If the user's name isn't available, like forgenerictypeAUTH_PROVIDER, the email address will be used instead.
Default: none
SHARE_ACCESSED_SUBJECT¶
SHARE_ACCESSED_SUBJECT specifies the email subject for the mails sent to the owner of a Web Portal share if the share gets accessed by an assignee for the first time and seal-email-service is enabled, for example Share accessed.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ACCESSED_SUBJECT
Available values: String
Default: none
SHARE_ACCESSED_TEXT¶
SHARE_ACCESSED_TEXT specifies the plain text template for emails sent to the owner of a Web Portal share if the share gets accessed by an assignee for the first time and seal-email-service is enabled.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ACCESSED_TEXT
Available values: String
Available placeholders:
-
{shareId}: ID of the share. If both, public and private links to shares, should be sent, it is adviced to use the{shareLink}placeholder instead. -
{shareLink}: Automatically generated link to the share. Depending on whether the share is private or public either a private or a public link will be generated. -
{shareName}: Name of the share given by the creator of the share. -
{userName}: Name of the user who accessed the share. If the user's name isn't available, like forgenerictypeAUTH_PROVIDER, the email address will be used instead.
Default: none
Example - example text with {shareLink} placeholder
Hello! {userName} accessed your share {shareName} at {shareLink}.
Example - usage of the {shareId} placeholder with a public link.
Hello! {userName} accessed your share "{shareName}" at https://myserver.com:3000/#/public/operator-webportal?view=share&shareId={shareId}.
Example - usage of the {shareId} placeholder with a private link.
Hello! {userName} accessed your share "{shareName}" at https://myserver.com:3000/#/service/operator-webportal?view=share&shareId={shareId}.
SHARE_ASSIGNED_HTML¶
SHARE_ASSIGNED_HTML specifies the HTML template for emails sent to the assignees of a Web Portal share if the seal-email-service is enabled.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ASSIGNED_HTML
Available values: String
Available placeholders:
-
{expirationDate}: End date of the share. After that date the share can't be accessed by its assignees anymore. The share will not automatically be deleted afterwards. Its owner can change the end date via the Web Portal UI to make it accessable again. IfAccess Notificationis enabled a new notification email will be sent in that case. -
{shareId}: ID of the share. For the structure of private and public links, refer to the examples for SHARE_ASSIGNED_TEXT. If both, public and private links to shares should be sent, it is adviced to use the{shareLink}placeholder instead. -
{shareLink}: Automatically generated link to the share. Depending on whether the receiver of the email is a registered user in the used OIDC either a private or public link will be generated and sent. -
{shareName}: Name of the share given by the creator of the share.
Default: none
SHARE_ASSIGNED_SUBJECT¶
SHARE_ASSIGNED_SUBJECT specifies the email subject for the mails sent to the assignees of a Web Portal share if the seal-email-service is enabled, for example Share assigned.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ASSIGNED_SUBJECT
Available values: String
Default: none
SHARE_ASSIGNED_TEXT¶
SHARE_ASSIGNED_TEXT specifies the plain text template for emails sent to the assignees of a Web Portal share if the seal-email-service is enabled.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/SHARE_ASSIGNED_TEXT
Available values: String
Available placeholders:
-
{expirationDate}: End date of the share. After that date the share can't be accessed by its assignees anymore. The share will not automatically be deleted afterwards. Its owner can change the end date via the Web Portal UI to make it accessable again. IfAccess Notificationis enabled a new notification email will be sent in that case. -
{shareId}: ID of the share. For the structure of private and public links, refer to the examples below. If public and private links to shares will be sent, it is adviced to use the{shareLink}placeholder instead. -
{shareLink}: Automatically generated link to the share. Depending on whether the receiver of the email is a registered user in the used OIDC either a private or public link will be generated and sent. -
{shareName}: Name of the share given by the creator of the share.
Default: none
Example - example text with placeholders
Hello! You received access to share "{shareName}". You can access it via this link: {shareLink}. The share will expire on {expirationDate}.
Example - usage of the {shareId} placeholder with a public link.
Hello! You received access to share "{shareName}". You can access it via this link: https://myserver.com:3000/#/public/operator-webportal?view=share&shareId={shareId}. The share will expire on {expirationDate}.
Example - usage of the {shareId} placeholder with a private link.
Hello! {userName} accessed your share "{shareName}" at https://myserver.com:3000/#/service/operator-webportal?view=share&shareId={shareId}. The share will expire on {expirationDate}.
SITE_COLLECTION¶
SITE_COLLECTION specifies the base URL to the SharePoint site collection.
The key is available for the seal-operator-sharepoint service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-sharepoint/tag/any/SITE_COLLECTION
Available values: String
<url>
Default: none
SMTP_PASSWORD¶
SMTP_PASSWORTspecifies the password for the user defined in SMTP_USERNAME to use with the SMTP server.
The key is available for the seal-email-service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/email-service/tag/any/SMTP_PASSWORT
Available values: String
Default: none
SMTP_PORT¶
SMTP_PORTspecifies the port of the SMTP server.
The key is available for the seal-email-service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/email-service/tag/any/SMTP_PORT
Available values: String
Default: 587
SMTP_SERVER¶
SMTP_SERVERspecifies the name of the SMTP server, for example, imap.strato.de
The key is available for the seal-email-service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/email-service/tag/any/SMTP_SERVER
Available values: String
Default: email-smtp.eu-central-1.amazonaws.com
SMTP_USERNAME¶
SMTP_USERNAME specifies the user to use with the SMTP server.
The key is available for the seal-email-service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/email-service/tag/any/SMTP_USERNAME
Available values: String
Default: none
SORT_COLLECTIONS_FIRST¶
SORT_COLLECTIONS_FIRST specifies if the directories are listed before the documents.
The key is available for the seal-operator-treeresolver service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-treeresolve/tag/any/SORT_COLLECTIONS_FIRST
Available values: Boolean
-
YThe directories are listed before the documents. This sorting is known from the Windows file explorer.
-
NThe items are not sorted according to their document type.
Default: N
SORT_METADATA¶
SORT_METADATA specifies a space-separated list of metadata keys used for sorting the items. The first metadata key has the highest priority for the sorting. With each metadata key, the sort type and the sort direction can be specified separated by the # character. Available values for the sort type are number for the numerical and string for the alphanumerical sorting. The default sort type is string. Available values for the sort direction are up and down. The default sort direction is up.
The key is available for the seal-operator-treeresolver service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-treeresolve/tag/any/SORT_METADATA
Available values: String
Default: none
Example - metadata
level#number#up Name first sorts the items by the level metadata key numerically upwards and, if the levels are identical, the items are sorted by the Name metadata key.
SORT_OVERALL¶
SORT_OVERALL specifies if the collected items are sorted over all items or in each directory.
The key is available for the seal-operator-treeresolver service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-treeresolve/tag/any/SORT_OVERALL
Available values: Boolean
-
YThe items are sorted over all items.
-
NThe items are sorted in each directory.
Default: N
STAMP_META¶
STAMP_META specifies if stamps are also applied to additional sheets, such as cover or trailer sheets.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/STAMP_META
Available values: Boolean
Default: N
STORAGE_SERVICE_NAME¶
STORAGE_SERVICE_NAME specifies the name of the service that will store the entries with their associated content for SEAL Web Portal. The value equals the SERVICE_NAME of the used storage service.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/STORAGE_SERVICE_NAME
Available values: String. Availabe values depend on the services installed.
Default: operator-fileupload
SYSTEMS¶
SYSTEMS specifies a subsection containing a list of PLOSSYS 4 systems. Every list entry stands for a P4 system and starts with a dash.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/SYSTEMS
Hint - multiple PLOSSYS 4 systems
For further information, refer to Multiple PLOSSYS 4 Backends.
Available sub-keys per system entry:
-
PLOSSYS_URL(mandatory) -
PLOSSYS_NAME(optional) -
TARGET_CONTENT_TYPE(optional) -
TARGET_FILE_KEY(optional) -
USER_NAME_KEY(optional)
Default: none
Example - configuration with multiple P4 backends
env:
service:
...
operator-p4:
tag:
any:
ACTION_EXECUTOR: P4
SYSTEMS:
- PLOSSYS_NAME: <system_1_name>
PLOSSYS_URL: 'https://<plossys_4_server_1_name>:3011'
- PLOSSYS_NAME: <system_2_name>
PLOSSYS_URL: 'https://<plossys_4_server_2_name>:3011'
...
Hint - structure in Consul
When setting the key via Consul another indexed subsection is needed since Consul doesn't know enumerations.
The same configuration as above transformed to Consul structure:
env:
service:
operator-p4:
tag:
any:
SYSTEMS:
0:
PLOSSYS_NAME: <system_1_name>
PLOSSYS_URL: 'https://<plossys_4_server_1_name>:3011'
1:
PLOSSYS_NAME: <system_2_name>
PLOSSYS_URL: 'https://<plossys_4_server_2_name>:3011'
The PLOSSYS_URL for the first system in Consul UI. Take notice of the emphasized breadcrumb line on top:
TARGET_CONTENT_TYPE¶
TARGET_CONTENT_TYPE specifies the PLOSSYS 4-specific job format.
Hint - multiple PLOSSYS 4 systems
In case of multiple PLOSSYS 4 systems the configuration differs, refer to SYSTEMS and Multiple PLOSSYS 4 Backends.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/TARGET_CONTENT_TYPE
Available values: String
-
application/rliFor a repro list
-
application/jsonFor a set collation
Default: application/json
TARGET_FILE_KEY¶
TARGET_FILE_KEY specifies the key where to put the names of local files (i. e. the files stored in the My Documents lists) when exporting to a repro list.
Hint - multiple PLOSSYS 4 systems
In case of multiple PLOSSYS 4 systems the configuration differs, refer to SYSTEMS and Multiple PLOSSYS 4 Backends.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/TARGET_FILE_KEY
Available values: String
<plossys_key>
Default: PLS_ORIG_NAME
TASK_CREATE_WITH_USER_DEFAULT¶
TASK_CREATE_WITH_USER_DEFAULT specifies if the tasks are created with the user defaults as metadata.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_CREATE_WITH_USER_DEFAULT
Available values: Boolean
-
YThe user defaults are used as metadata of new tasks.
-
NThe system defaults are used as metadata of new tasks.
Default: Y
TASK_TIMEOUT¶
TASK_TIMEOUT specifies the time interval after which the seal-operator-server service looks for finished tasks to be deleted. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TIMEOUT
Available values: string
<time_interval_and_unit>
Default: 1h
TASK_TTL_ABORTED¶
TASK_TTL_ABORTED specifies the time interval after which an aborted task will be deleted by the seal-operator-server service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TTL_ABORTED
Available values: String
-
<time_interval_and_unit>Aborted tasks will be deleted after the specified time.
-
0Aborted tasks never will be deleted.
Default: 1w
TASK_TTL_COMPLETED¶
TASK_TTL_COMPLETED specifies the time interval after which a completed task will be deleted by the seal-operator-server service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TTL_COMPLETED
Available values: String
-
<time_interval_and_unit>Completed tasks will be deleted after the specified time.
-
0Completed tasks never will be deleted.
Default: 1w
TASK_TTL_FAILED¶
TASK_TTL_FAILED specifies the time interval after which a failed task will be deleted by the seal-operator-server service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TTL_FAILED
Available values: String
-
<time_interval_and_unit>Failed tasks will be deleted after the specified time.
-
0Failed tasks never will be deleted.
Default: 1w
TASK_TTL_OPEN¶
TASK_TTL_OPEN specifies the time interval after which an open task will be deleted by the seal-operator-server service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TTL_OPEN
Available values: String
-
<time_interval_and_unit>Open tasks will be deleted after the specified time.
-
0Open tasks never will be deleted.
Default: 0
TASK_TTL_PROCESSING¶
TASK_TTL_PROCESSING specifies the time interval after which a processing task will be deleted by the seal-operator-server service. The time interval has to be specified including the unit. For the available units, refer to Units at the top of the page.
The key is available for the seal-operator-server service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-server/tag/any/TASK_TTL_PROCESSING
Available values: String
-
<time_interval_and_unit>Processing tasks will be deleted after the specified time.
-
0Processing tasks never will be deleted.
Default: 1w
TLS_DIR¶
TLS_DIR specifies the directory containing the certificate files necessary for the secure transfer within SEAL Operator.
The key is available for all services.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/any/tag/any/TLS_DIR
Available values: String
<dir_name>
The directory contains the following files:
-
key.pemFile containing the private key
-
cert.pemFile containing the certificate
-
ca.pem(optional)File containing the CA certificate
Default: none
Hint - certificate files contained in delivery
The self-signed certificates contained in delivery are hard-coded. The tls directories contained in delivery only contain examples which certificate files are required and how they look like.
Hint - tls certificate fallback chain
TLS_EXTERNAL_DIR -> TLS_DIR -> built-in certificates
Caution - security gap
Using the pre-installed self-signed certificate in a productive system is a serious security gap!
TLS_EXTERNAL_DIR¶
TLS_EXTERNAL_DIR specifies the directory containing the external certificate files necessary for the services handling external requests.
The key is available for the following services:
- seal-operator-ui
- seal-operator-server
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
-
dc/home/env/service/operator-server/tag/any/TLS_EXTERNAL_DIR -
dc/home/env/service/operator-ui/tag/any/TLS_EXTERNAL_DIR
Instead of setting the key for each service, it can also be specified here once and for all:
dc/home/env/service/any/tag/any/TLS_EXTERNAL_DIR
Available values: String
<dir_name>
The directory contains the following files:
-
key.pemFile containing the private key
-
cert.pemFile containing the certificate
-
ca.pem(optional)File containing the CA certificate
Default: none
Hint - certificate files contained in delivery
The self-signed certificates contained in delivery are hard-coded. The tls directories contained in delivery only contain examples which certificate files are required and how they look like.
Hint - tls certificate fallback chain
TLS_EXTERNAL_DIR -> TLS_DIR -> built-in certificates
Caution - security gap
Using the pre-installed self-signed certificate in a productive system is a serious security gap!
TRUSTED_CLIENT¶
TRUSTED_CLIENT specifies the client name configured in the OIDC identity provider for granting access via access token.
The key is available for the following services:
seal-operator-fileuploadseal-operator-serverseal-operator-sharepoint
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-fileupload/tag/any/TRUSTED_CLIENTdc/home/env/service/operator-server/tag/any/TRUSTED_CLIENTdc/home/env/service/operator-sharepoint/tag/any/TRUSTED_CLIENT
Available values: String
<client_name>
Default: operator
UI_BASE_URL¶
UI_BASE_URL specifies the base URL of the Web Portal user interface. Only necessary if the {shareLink} placeholder is used in an email template and the automatic detection of this URL is prone to fail (e.g. when shares are created through a batch process).
The key is available for the following service:
seal-operator-webportal
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/UI_BASE_URL
Available values: String
<ui_base_url>
Default: none
Example
env:
service:
operator-webportal:
tag:
any:
UI_BASE_URL: 'https://myserver.com:3000'
...
USER_NAME_KEY¶
USER_NAME_KEY specifies the key where to put the name of the logged-in user when exporting to a repro list. By default, no user is set in a repro list passed to PLOSSYS 4. If you want the name of the logged-in user to be set in the repro list, specify the repro list key where to put the user name (e. g. PLS_USERNAME). The user name will then be set regardless of an already existent user name in the repro list.
Hint - multiple PLOSSYS 4 systems
In case of multiple PLOSSYS 4 systems the configuration differs, refer to SYSTEMS and Multiple PLOSSYS 4 Backends.
The key is available for the seal-operator-p4 service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-p4/tag/any/USER_NAME_KEY
Available values: String
<plossys_key>
Default: none
WEBPORTAL_CLIENT_ID¶
WEBPORTAL_CLIENT_ID specifies the client name configured in the OIDC identity provider for granting access via access token.
Hint - different usage of AUTH_CLIENT_ID and WEBPORTAL_CLIENT_ID
AUTH_CLIENT_ID is used for setting up the seal-operator-server connection, while WEBPORTAL_CLIENT_ID is used only for storing files in the fileupload store.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/WEBPORTAL_CLIENT_ID
Available values: String
<client_id>
Default: seal-webportal
WEBPORTAL_CLIENT_SECRET¶
WEBPORTAL_CLIENT_SECRET specifies the client secret for the respective WEBPORTAL_CLIENT_ID as configured in the OIDC identity provider for granting access via access token.
The key is available for the seal-operator-webportal service.
In Consul, the key is specified here. If the key does not exist yet, you have to create it:
dc/home/env/service/operator-webportal/tag/any/WEBPORTAL_CLIENT_SECRET
Available values: String
<client_secret>
Default: 1f86ba87-64f2-4c3f-9c92-bbd5befdf6f7